
BLOG
CORL Releases New NIST 800-53 Rev 5 Vendor Questionnaire
Published On November 23, 2021

CORL is continually innovating and updating our capabilities to provide the healthcare industry’s leading Vendor Risk Management (VRM) solution set. We are pleased to announce that the following innovations have been released:
| Product Name: CORL Vendor Portal v1.0
Component: NIST 800-53 Rev 5 Vendor Security Questionnaire (VSQ) Overview: The CORL Vendor Portal now includes a new NIST SP 800-53 Rev 5 Vendor Security Questionnaire (VSQ). The new vendor questionnaire is 351 questions and includes the following features:
|
Background
The National Institute of Standards and Technology (NIST) has announced an updated version of their flagship security controls framework NIST Special Publication (SP) 800-53. The new version, Revision 5 or “Rev 5”, update is the first overhaul of the NIST SP 800-53 framework in over seven years and represents critical updates that reflect the modern cyber threat landscape. A major addition in this revision includes an entire security controls “family” dedicated to Supply Chain Risk Management (SR).
A complete rundown of the new NIST SP 800-53 Rev 5 controls and a comparison to NIST SP 800-53 Rev 4 can be found in our related blog post: NIST SP 800-53 Rev 5: New Supply Chain Control Requirements.
New Features
The new NIST SP 800-53 Rev 5 vendor questionnaire is 351 questions and includes the following features:
1. Rev 4 to Rev 5
The vendor questionnaire has been updated from NIST SP 800-53 Rev 4 controls to new Rev 5 control set
- According to NIST, Rev 5 is not just a minor update but is a “complete renovation” [2] of the standard. Rev 5 adds more than 45 new base controls, 150 new control extensions, and approximately 100 new parameters to existing controls.
- The most significant updates include the addition of controls around third-party risk and supply chain, privacy, and new “state of the practice” areas like cyber resiliency, secure systems design, and governance models. The framework updates have also been designed to scale and apply to a variety of systems and applications from largescale IT and cloud infrastructures down to individual mobile and IoT devices.
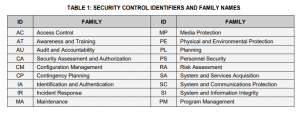
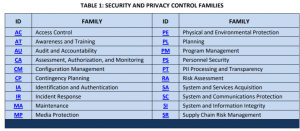
- Here is a quick view of the vendor questionnaire control family changes from Rev 4 to Rev 5.
NIST SP 800-53 Rev 4 Control Families
NIST SP 800-53 Rev 5 Control Families
2. New Privacy Control Category
The vendor questionnaire now includes a new domain for privacy controls that NIST indicates has the following benefits:
- Consolidating the control catalog: Information security and privacy controls are now integrated into a seamless, consolidated control catalog for systems and organizations. The privacy controls in Appendix J of Revision 4 have been incorporated into a new privacy family and the existing Program Management family. Some of the privacy controls were also incorporated into current security controls - allowing the controls to serve both the security and privacy communities as well as achieving more efficient control implementation.
3. New Supply Chain Risk Management Category
The vendor questionnaire now includes a new domain for Supply Chain Risk that NIST indicates has the following benefits:
- Integrating supply chain risk management: Rev 5 establishes a new Supply Chain Risk Management (SCRM) control family and integrates supply chain risk management aspects throughout the other control families to help protect system components, products, and services that are part of critical systems and infrastructures. The SCRM controls help ensure that security and privacy requirements, threats, and other concerns are addressed throughout the system development life cycle and the national and international supply chains.
4. New Controls for Runtime Application Self-Protection (RASP) and Interactive Application Security Testing (IAST)
These new control areas in the vendor questionnaire are designed to modernize security control requirements for application security and related application security testing processes.
5. Control Consolidation
The consolidation of controls and logical restructuring of the framework is a necessary form of “hygiene” for any control framework that strives to keep up with complex and evolving business and threat landscapes. NIST describes the control consolidation updates as follows:
- Consolidating the control catalog: Information security and privacy controls are now integrated into a seamless, consolidated control catalog for systems and organizations. The privacy controls in Appendix J of Revision 4 have been incorporated into a new privacy family and the existing Program Management family. Some of the privacy controls were also incorporated into current security controls - allowing the controls to serve both the security and privacy communities as well as achieving more efficient control implementation
6. Outcome-based Controls
The movement to outcomes-based controls represents a fundamental mindset shift that will help organizations to move away from a focus on tactical “busy work” and towards strategic outcomes that can measurably reduce risk. NIST describes the outcomes-based model as follows:
- Making controls outcome-based: Rev 5 accomplishes this by removing the entity responsible for satisfying the control (i.e., information system, organization) from the control statement - thus focusing on the protection outcome to be achieved by the application of the control. Note that for historical continuity, Appendix C, Control Summaries now includes an “implemented by [system/organization]” column.
More details about the NIST SP 800-53 Rev 5 vendor questionnaire and control set can be found in the following resources:
- CORL Blog Post | NIST SP 800-53 Rev 5: New Supply Chain Control Requirements
- NIST 8000-53 Rev 5 Source Documentation
SOURCES
[1] https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r5.pdf
[2] https://www.nist.gov/blogs/cybersecurity-insights/next-generation-security-and-privacy-controls-protecting-nations