BLOG
Healthcare Takes It on the Chin with Supply Chain Breaches
Published On June 21, 2021
Blog Post by Devon Wijesinghe, Chief Transformation Officer at CORL Technologies
Cyberattacks on the supply chain have been growing exponentially in the last several years. These attacks had introduced substantial social and political implications, as we saw with the recent attack against the Colonial Pipeline [1] that disrupted the supply of oil and gas for the southeastern U.S. region.
Healthcare has been hit the hardest of all industry segments at a time when we need to be firing on all cylinders to address and recover from a global pandemic. The supply chain attacks, in particular, have a greater impact to healthcare entities due to our increased dependency on third-party solutions to provide core capabilities for the care, treatment, and administration of healthcare delivery.
Supply chain breaches began as a threat to patient data and confidentiality, and have now evolved into events that put patient safety and operations routinely at risk. Healthcare’s dependency on cloud-hosted solutions to support its movement to digital healthcare models have exacerbated the matter.
Regulators like OCR are also shifting focus to the management of third-party risks for covered entities and business associates alike.
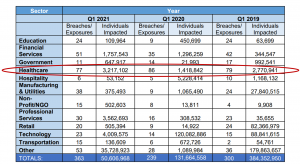
Healthcare is Hardest Hit Industry Sector
A new report from the Identity Theft Research Center (ITRC) cites healthcare as the industry sector with the highest volume of breach events in the past two years. [2]
The ITRC report notes a 42 percent rise in the number of supply chain attacks. This includes supply chain attacks at 27 third-party vendors in Q1 2021, including global IT provider Accellion, which impacted 137 US organizations and 7 million individuals (more on that breach is provided below). For some context on trending of attacks, there were 19 supply chain attacks in Q4 2020.
Top Supply Chain Breaches Impacting Healthcare Entities in 2020-2021
Healthcare has been grappling with an incessant pounding of supply chain attacks. Some of the more notable attacks impacting healthcare specifically in the last year include:
- SolarWinds - the sophisticated attack leveraged a compromise of the SolarWinds Orion software updates to create a backdoor into the networks that leverage the popular network monitoring solution. The malicious code was embedded in SolarWinds software updates and pushed down to unsuspecting organizations from March through June 2020. The Orion platform is reportedly used by over 18,000 organizations in the public and private sectors including many healthcare entities.
- Microsoft Exchange Server - over 30,000 organizations, including healthcare entities, were infiltrated by a Chinese-affiliated espionage group via zero-day vulnerabilities in Microsoft Exchange email servers in March of this year. The attack had wide-ranging impacts for healthcare organizations, a majority of which use Microsoft to provide email services. This attack’s immediate effect was to allow the hackers to access organizational emails, which could reveal sensitive corporate information including e-PHI and to install backdoors as a base for future attacks.
- Accellion File Transfer - Breaches of Accellion’s File Transfer Appliance led to infiltration of dozens of customer networks in March of this year. Accellion allowed the malicious actors to gain access to about a third of Accellion’s client base, or almost 100 hundred organizations, of which about twenty five received ransom threats over the data they had stolen through the platform.
- Blackbaud - Blackbaud experienced one of the largest ransomware attacks of 2020 which saw attackers present in their network from February through June of that same year. Blackbaud is a leading provider of fundraising support and solutions and has a substantial presence servicing the healthcare industry. CORL routinely sees Blackbaud show up in the vendor portfolios that we manage for our clients. The organization paid the attackers to restore systems and erase the stolen patient data.
Vulnerable Third-Party Software Used for Ransomware Infection
Third-party software weaknesses are also a leading source of ransomware infection from Russian malware agents according to the CISA. [3] Some of the top third-party software exploits used to introduce malware into healthcare entities include:
- Citrix application delivery and Citrix Gateway - directory traversal to run code with elevated permissions
- Fortinet Fortigate VPN - download system files via resource requests
- VMware workspace or OneAccess - command injection lets lower-level users run code at system admin level
- Synacor Zimbra Collaboration Suite - XML escalation vulnerability
- Pulse Secure VPN - grants read access to files without authentication
CORL’s Managed Services & Next Generation Exchange of Vendor Risk Data
In order to combat these growing supply chain risks, CORL has developed a proprietary data clearinghouse that provides with access to assessment results of over 79,000 vendor assessments CORL has conducted. Each year, CORL conducts thousands more vendor risk assessments on behalf of our clients. Chances are very high that we have already assessed a substantial portion of your existing and new vendors from a security, risk, and compliance perspective.
CORL’s tech-enabled managed services and next generation exchange of vendor risk data allows healthcare entities to:
- Prioritize vendors for assessment and remediation
- Make informed supply chain risk decisions
- Scale vendor risk programs
- Report on vendor risk across the entire vendor portfolio
- Drive and track remediation
- Validate controls and gain assurance
- Track KPI, KRI, and SLA metrics on program performance
- Identify trends in vendor types to anticipate breaches
- Save time, money, and resources
- Accelerate assessment turnaround times
Contact our team here at CORL to learn more about our managed services and next generation exchange for healthcare vendor risk data that gets results with regulatory compliance and lowers supply chain risks.
SOURCES
[1] Cyberattack Forces a Shutdown of a Top U.S. Pipeline
[2] Data Breach Resources to Help Make Better Decisions | Trend Analysis
[3] Russian SVR Targets U.S. and Allied Networks