
BlogTPRM
Top 10 Healthcare Supplier Risk Management Challenges Facing Providers in 2025
3 Minute Read
Read Top 10 Healthcare Supplier Risk Management Challenges Facing Providers in 2025TPRM
By CORL Technologies | August 3, 2023
Purpose:
The Health3PT Initiative conducted the survey summarized on the following pages to identify issues in the current Healthcare Third-Party Cyber Risk Management environment and drive towards improved collaborative solutions.
You’re invited to review respondent results to gain valuable insights from other healthcare information security professionals that can help your organization create a healthier, lower-risk ecosystem for all participants.
| 55% | of healthcare organizations experienced a third-party breach in the past year1 |
| $10.1M | is the average cost of a healthcare data breach2 |
| 90% | of the most significant healthcare breaches in 2022 were tied to vendors3 |
1 https://www.hipaajournal.com/55-of-healthcare-organizations-suffered-a-third-party-data-breach-in-the-past-year/
2 https://www.ibm.com/reports/data-breach
3 https://www.scmagazine.com/feature/breach/most-of-the-10-largest-healthcare-data-breaches-in-2022-are-tied-to-vendors
Third-party risks associated with supply chain vendors and service providers critically threaten and challenge healthcare cybersecurity, data protection, and the safety of patient records. Unfortunately, today’s methods to manage third-party risk exposure are burdensome and inadequate.
There are significant blind spots relating to third-party information security risk because:
To establish and promote trusted cyber security practices throughout the third-party healthcare ecosystem, professionals from leading healthcare organizations joined to form the Health 3rd Party Trust (Health3PT) Initiative. The objectives of the Health3PT-sponsored survey were to identify common issues around healthcare TPRM and gather respondent insights on collaborative ways to refine and implement meaningful solution improvements.
1. Covered Entities and Business Associates
Both groups share a strong belief that current TRPM processes are inefficient and ineffective in preventing data breaches:
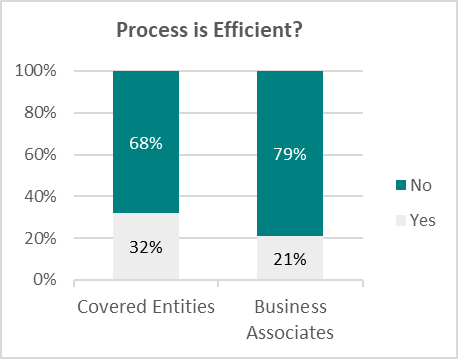
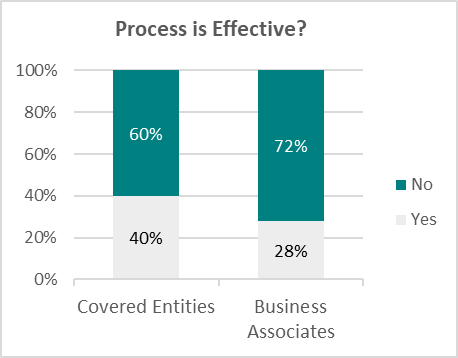
2. Suggested Improvements from Both Sides
Survey results point to several efficiencies that can create a more collaborative approach that helps streamline and standardize the risk management process for Covered Entities and Business Associates.
The survey is designed to capture perspectives from healthcare Covered Entities and Business Associates.
Covered Entities. Under HIPAA rules, Covered Entities are defined as (1) health plans, (2) healthcare clearinghouses, and (3) healthcare providers who electronically transmit any health information in connection with transactions for which HHS has adopted standards. Covered Entities must require Business Associates with whom they partner to meet applicable HIPAA requirements.
Business Associates. Under HIPAA rules, Business Associates are defined as a person or entity that performs certain functions or activities that involve the use or disclosure of protected health information on behalf of, or provides services to, a covered entity.
The survey responses not only help validate why and where third-party risk management methodologies can be improved, but they also reveal where opportunities exist that can build more efficient and practical approaches to reduce cyber risk across the healthcare ecosystem.
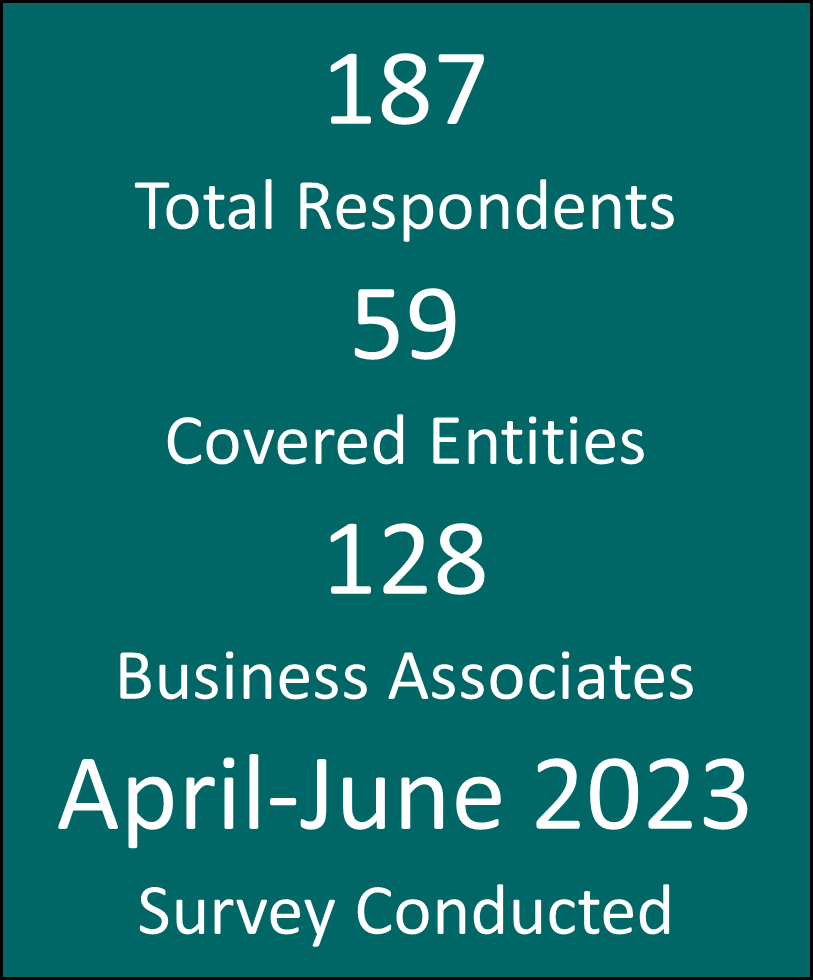
Survey questions are designed to gain an understanding of the standard practices used by healthcare organizations to assess the cyber risk of their suppliers and how those suppliers provide assurances of their cyber security capabilities. The complete data set in the Appendix will provide insights into how current practices reveal gaps in assessment quality, frequency, and continuous monitoring of remediation efforts that are central to more effective risk management. This section focuses on the top-level findings around the most significant challenges and where organizations need help to make TPRM more effective.
The Health3PT survey gathered information from Covered Entities and Business Associates to identify pain points in the current process and pinpoint opportunities for improvement. In addition, each group was asked how satisfied they were that their organization could address the common challenges associated with the current TPRM processes.
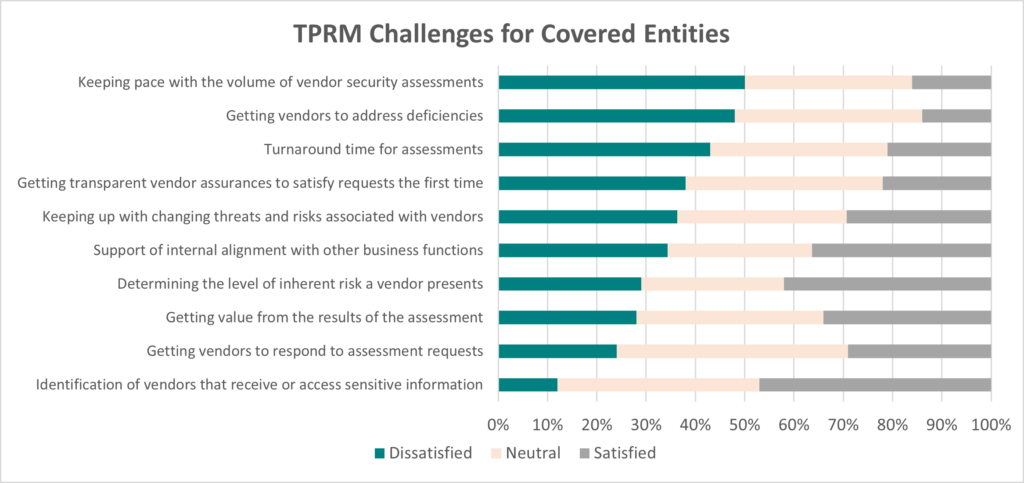
Covered Entities: From the table below, you can see that most organizations need help with these aspects of TPRM:
Receiving transparent assurances from vendors to satisfy the request the first time.
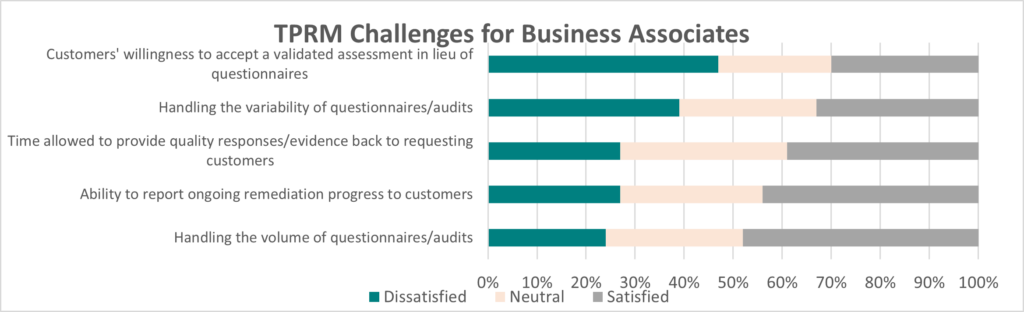
Business Associates: From the table shown below, you can see that most organizations need help with these aspects of TPRM:
The State of Healthcare Third-Party Cyber Risk Management survey confirms and highlights several significant findings:
By combining survey learnings along with perspectives shared at a recent Vendor Risk Management Summit and long-standing experience from healthcare information security and risk management professionals, Health3PT recommends the following Best Practices for TPRM success:
Establishing and adopting these more effective and efficient TPRM processes will transition TPRM in healthcare from a superficial check-the-box exercise that exposes organizations to unnecessary risks to more robust, collaborative information protection programs that will ultimately benefit all participants across the healthcare community.
The guiding principles for the Health3PT Initiative are…
The Health 3rd Party Trust Initiative is governed by a council of professionals from leading care providers, health systems, and other healthcare organizations committed to reducing third-party information security risk with more reliable and consistent assurances. health3pt.org
This Appendix shows each survey’s exact questions and answers for Covered Entities and Business Associates.
| Challenge | Dissatisfied | Neutral | Satisfied |
|---|---|---|---|
| Identification of vendors that receive or access sensitive information | 12% | 41% | 47% |
| Determining the level of inherent risk a vendor presents? | 29% | 29% | 42% |
| Getting vendors to respond to assessment requests? | 24% | 47% | 29% |
| Receiving transparent assurances from vendors to satisfy the request the first time | 38% | 40% | 22% |
| Keeping pace with the volume of vendor security assessments | 50% | 34% | 16% |
| Turnaround time for assessments | 43% | 36% | 21% |
| Getting value from the results of the assessment | 28% | 38% | 34% |
| Getting vendors to address deficiencies | 48% | 38% | 14% |
| Support of internal alignment with other business functions | 34% | 29% | 36% |
| Keeping up with changing threats and risks associated with vendors | 36% | 34% | 29% |
2. Do you have contractual language for security requirements that must be met before onboarding a vendor?
3. What forms of assessments do you accept from your vendors today? (Choose all that apply)
4. If you use surveys or questionnaires to assess third-party risk, what framework(s) or standards are they based on? (Choose all that apply)
5. What percentage of your vendor population does your organization assess?
6. What percentage of your vendor population is regularly reassessed (at least annually)?
7. How do you obtain updates on remediations from your vendors?
8. Do you believe your current vendor risk management process is efficient (value vs. effort)?
9. Do you believe your current vendor risk management process is effective in terms of preventing data breaches?
10. Please indicate the level of importance for each statement below in terms of making vendor risk management more efficient and effective.
| Statement | Unimportant | Neutral | Important |
|---|---|---|---|
| Create norms around inherent risk and vendor tiering in the TPRM ecosystem | 3% | 12% | 85% |
| Standardize around third-party validated assurance mechanisms instead of one-off self-attested questionnaires to improve efficiency and effectiveness on both sides | 5% | 10% | 85% |
| Receive vendor assessment results electronically to gain faster time to insights and enable your resources to do higher value risk management activities | 9% | 7% | 84% |
| Drive constant security improvement through continuous monitoring and remediation reporting | 2% | 14% | 84% |
11. What is your role in the organization?
12. In which department do you work?
13. What is the size of your organization in annual revenue?
| Challenge | Dissatisfied | Neutral | Satisfied |
|---|---|---|---|
| Handling the volume of questionnaires/audits | 24% | 28% | 48% |
| Handling the variability of questionnaires/audits | 39% | 28% | 33% |
| Time allowed to provide quality responses/evidence back to requesting customers | 27% | 34% | 39% |
| Ability to report ongoing remediation progress to customers | 27% | 29% | 44% |
| The willingness of customers to accept validated assessments and certifications in lieu of their proprietary control questionnaires | 47% | 23% | 30% |
2. What percentage of your customers ask for cybersecurity assurances to enable a business relationship?
3. What percentage of your customers regularly reassess your organization or ask to see progress on remediation?
4. What assurance mechanisms do you provide to fulfill customer cybersecurity requests (Check all that apply)
5. If you selected C or D in question 4, what percentage of your customers will forgo the use of their proprietary questionnaire during security due diligence if you provide a third-party validated assessment or certification?
6. Do you believe the current process for providing cyber risk assurances is efficient?
7. Do you believe the current process of providing cyber risk assurances effectively prevents data breaches?
8. Please indicate the level of importance for each of the potential solution elements below.
| Statement | Unimportant | Neutral | Important |
|---|---|---|---|
| A collaborative approach to understanding the assurance requirements of your organization based on the inherent risk you present to your customer. | 7% | 12% | 81% |
| Standardize third-party validated assurance mechanisms that cover the scope of the business relationship instead of one-off questionnaires to improve efficiency and effectiveness on both sides. | 5% | 8% | 87% |
| Ability to share your assessment results electronically to provide your customer faster time to insights and decision making. | 8% | 11% | 81% |
9. What is your role in the organization?
10. What is the size of your organization in annual revenue?
11. What is your business category?
 CORL Technologies
CORL Technologies
CORL transforms TPRM chaos into clarity
CORL is a leading provider of vendor risk management solutions for the healthcare industry. CORL gets results by scaling organizational and vendor risk programs through our healthcare vendor risk clearinghouse solution, dashboard reporting that business owners can understand, and proven workflows that drive measurable risk reduction. CORL accelerates the speed of vendor risk assessments and holds vendors accountable for remediating risk exposures.
Related Posts

BlogTPRM
By CORL Technologies | August 14, 2025
3 Minute Read
Read Top 10 Healthcare Supplier Risk Management Challenges Facing Providers in 2025BlogCompliance
By CORL Technologies | June 24, 2025
5 Minute Read
Read Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment Suite
BlogTPRM
By CORL Technologies | May 19, 2025
2 Minute Read
Read More Than a Checkbox: Why Right-Sizing Vendor Risk Remediation Is the Key to Smarter TPRM
Webinars
WEBINAR H3PT Presents: Operationalizing TPRM for Success Join us for a focused, real-world conversation with healthcare security and risk leaders tackling today’s most pressing TPRM challenges. This session will bring together a small panel of experts for an insightful discussion on how to strengthen third-party risk programs in an evolving threat landscape. This won’t be […]