BlogCompliance
Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment Suite
5 Minute Read
Read Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment SuiteCompliance
By CORL Technologies | May 20, 2021
Recent high-profile supply chain attacks have heightened awareness of third-party vendor cybersecurity and privacy risks on a global scale. However, breaches and vulnerabilities in the supply chain have been on the radar for several years and have led to the development of slew of new regulations and standards.
In this blog post, we will give a quick rundown of some of the latest regulations, standards, and guidance targeting supply chain risks from a federal and global standpoint. Our overview includes discussion of two executive orders from President Biden, a proposed EU GDPR directive, NIST 800-53 standard updates, a UN directive on cybersecurity, a CISA report on supply chain risk, and implications for proposed changes to the HIPAA Privacy Rule and OCR enforcement.
President Biden issued a supply chain executive order in February of this year titled, America’s Supply Chains [1]. The order states that United States needs resilient, diverse and secure supply chains to ensure economic prosperity and national security.
The executive order highlights cyber-attacks in particular and calls for renewing the National Security Council system. It also mandates that government entities conduct supply chain risk assessments in the next hundred days across several departments, including Commerce, Energy, Defense, Agriculture and our favorite Health and Human Services. The Department of Health and Human Services (HHS) assessment in particular is required to focus on the risks to the pharmaceutical supply chain given the vaccine development and distribution criticality that’s going on at present.
The order also requires a risk assessment of the supply chain’s reliance on digital products that may be vulnerable to failures or exploitation.
At CORL, we think this is a long overdue response from the federal level to the inundation of attacks of a supply chain that we’ve seen from cyber criminals and nation states like Russia, China including attacks on SolarWinds, Microsoft Exchange, and the coordinated ransomware attacks in late 2020. This requirement for assessment, corrective action plan, coupled with some increased governance and oversight that they’re setting up here with that Security Council is going to be a first step in the part of a larger response that will include other diplomatic and economic pressures on those attacking our critical infrastructure, including health care.
President Biden issued a second executive order [2] for the year that includes supply chain risk content, but also covers a much larger range of cybersecurity mandates.
The directive provides sweeping updates to supply chain risk requirements in section 4 as follows:
Enhancing Software Supply Chain Security. (a) The security of software used by the Federal Government is vital to the Federal Government’s ability to perform its critical functions. The development of commercial software often lacks transparency, sufficient focus on the ability of the software to resist attack, and adequate controls to prevent tampering by malicious actors. There is a pressing need to implement more rigorous and predictable mechanisms for ensuring that products function securely, and as intended. The security and integrity of “critical software”—software that performs functions critical to trust (such as affording or requiring elevated system privileges or direct access to networking and computing resources)—is a particular concern. Accordingly, the Federal Government must take action to rapidly improve the security and integrity of the software supply chain, with a priority on addressing critical software.
Key provisions in the executive order include requirements for government entities to:
The European Union has issued pending directives and legislation that has expansive scope that is expected to be passed later this summer. It’s called the EU Directive on Mandatory Human Rights, Environmental and Good Governance, and Due Diligence, and it’s deployed alongside Germany’s corresponding corporate due diligence act.
This may change the way that third party risk programs are designed globally and could impact the approach for health care organizations in the US and abroad for sure, in a couple of different ways. The legislation is reported to have some serious teeth for non-compliance above and beyond traditional GDPR that will require organizations to implement thorough and continuous due diligence of third-party relationships in the context of environmental practices, social and human rights and governance to address corruption
The new directive is going to require the development of a robust third-party risk management program. The draft documentation states that due diligence should not be a box-ticking exercise, but should consist of an ongoing process and assessment of risks and impacts which are dynamic and may change on account of new business relationships or contextual development.
The directive is expected to become effective later this summer.
The National Institute of Standards and Technology (NIST) released an updated version of their flagship security controls framework NIST Special Publication (SP) 800-53 in late 2020. The new version, Revision 5 or “Rev 5”, update is the first overhaul of the NIST SP 800-53 framework in over seven years and represents critical updates that reflect the modern cyber threat landscape.
Rev 5 establishes a new Supply Chain Risk Management (SCRM) control family and integrates supply chain risk management aspects throughout the other control families to help protect system components, products, and services that are part of critical systems and infrastructures. The SCRM controls help ensure that security and privacy requirements, threats, and other concerns are addressed throughout the system development life cycle and the national and international supply chains.
The addition of supply chain risk management controls to the NIST SP 800-53 catalog is a much needed and long overdue adjustment to reflect the industry’s dependence on third-party vendors.
The U.N. has taken action on cyber-attacks targeting the supply chain by establishing and agreeing upon accepted standards for nation state online behavior in their March 2021 Final Substantive Report [3]. While the rules alone will not stop nation states from attacking, they may lay the groundwork for some enforcement and deterrence for large scale attacks like we saw against SolarWinds and Microsoft that have been attributed to nation states, Russia and China, respectively.
The new UN rules set requirements to protect the information communications technology or ICT supply chain, as they call it. It’s important to note that this isn’t a knee-jerk reaction from the UN. These rules have been in the works for over two years by the UN’s open-ended working group on Cybersecurity, and they’ve been updated five years ago as well. The rules specifically recognize the need to protect health care from cyber-attacks. It’s worth noting that the US is not the only victim of such attacks as the new report cites attacks on hospitals in the Czech Republic and Spain, Thailand and even against the World Health Organization.
The US Cyber Security and Infrastructure Security Agency (CISA) released a new report this month that provides guidance for managing supply chain risk. The report is titled Defending Against Software Supply Chain Attacks [4] and provides an overview of software supply chain risks and recommendations on how software customers and vendors can use the NIST Cyber Security Chain Supply Chain Risk Management Framework, or C-SCRM and the Secure Software Development Framework (SSDF) to identify, assess and mitigate software supply chain risks.
The report includes a list of supply chain life cycles and threats, areas, and historical context for supply chain attacks.
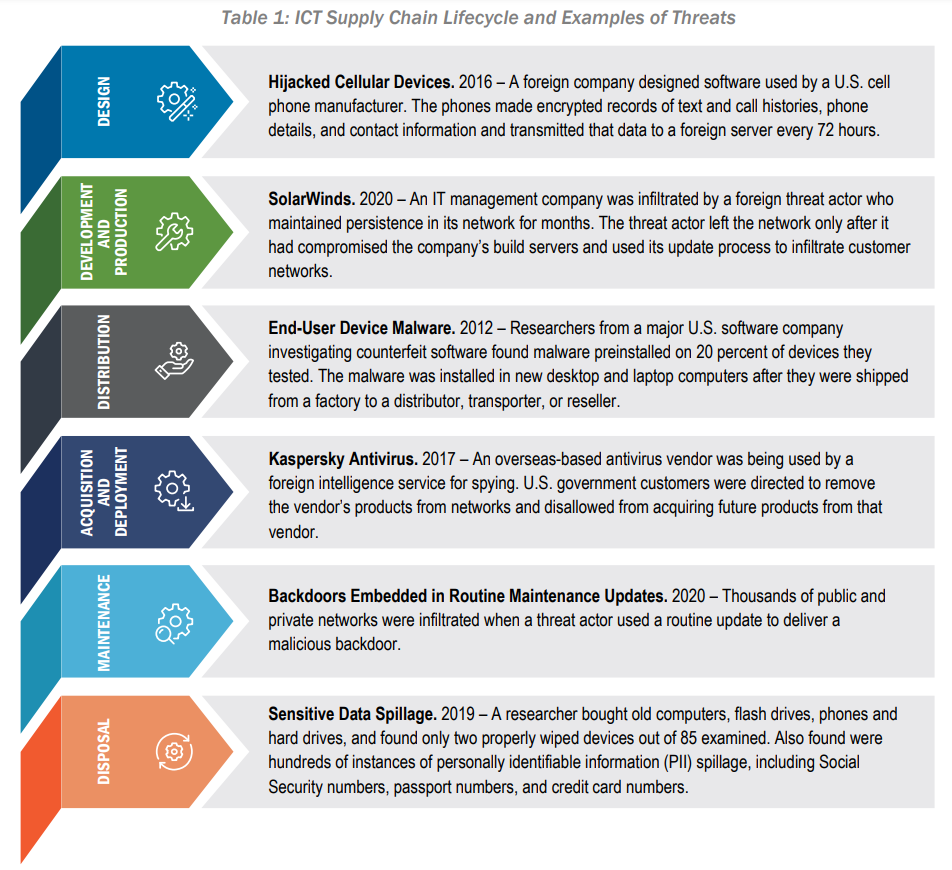
Source: Defending Against Software Supply Chain Attacks, CISA and the National Institute of Standards and Technology (NIST)
The report also highlights self-signed certificate ass a common attack method used to circumvent traditional trust models with SSL and other certificate authentication. It notes that this is a particularly favored approach for attackers out of China to leverage those self-signed certificates to bypass trust protocols.
They also note that compromising open-source code is another common threat vector. Attackers insert malicious code into public code libraries like Python libraries. And these are these libraries are common accelerators for developers that can reuse public code for common tasks and functions.
The report also talks about privileged access being a weakness for many applications and systems in the supply chain This is a ripe source for attacks against the supply chain, which can lead directly to the escalation of privileges on company networks.
The report further provides in-depth recommendations for software customers and vendors and next steps for prevention, mitigation, resilience and much more.
The Office for Civil Rights (OCR) has had third-party business associate risks and compliance on the radar for several years. OCR has targeted enforcement of covered entities’ management of third-party business associate agreements and contracts in 2019 through 2021.
New Interoperability and information blocking rules are also changing the way in which healthcare entities must share patient information across electronic health records and personal healthcare applications. Security and privacy requirements must be considered as patient information gets pushed downward into the technology supply chain with a host of new apps and providers flooding the market.
Proposed changes to the HIPAA Privacy Rule including implications for the release of patient information via third party business associates and the right to access information by patients. There are several other proposed provisions that impact third-party vendor and business associates. We discussed these new standards and regulations as part of a recent webinar on the HIPAA Privacy Rule proposed updates. You can access the replay of this session here: Proposed Modifications to the HIPAA Privacy Rule.
These regulations and standards are just the tip of the iceberg for what we can expect to see with supply chain risk guidance and requirements in the next several years.
Contact our team here at CORL to learn more about our managed services and next generation exchange for healthcare vendor risk data that gets results with regulatory compliance and lowers supply chain risks.
[1] America’s Supply Chains: A Presidential Document by the Executive Office of the President
[2] Improving the Nation’s Cybersecurity: A Presidential Document by the Executive Office of the President
[3] United Nations General Assembly: Open-ended working group on developments in the field of information and telecommunications in the context of international security
[4] Defending Against Software Supply Chain Attacks, CISA and the National Institute of Standards and Technology (NIST)
 CORL Technologies
CORL Technologies
CORL transforms TPRM chaos into clarity
CORL is a leading provider of vendor risk management solutions for the healthcare industry. CORL gets results by scaling organizational and vendor risk programs through our healthcare vendor risk clearinghouse solution, dashboard reporting that business owners can understand, and proven workflows that drive measurable risk reduction. CORL accelerates the speed of vendor risk assessments and holds vendors accountable for remediating risk exposures.
Related Posts
BlogCompliance
By CORL Technologies | June 24, 2025
5 Minute Read
Read Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment Suite
BlogCompliance
By CORL Technologies | April 23, 2025
2 Minute Read
Read The Power of Human + AI: CORL’s Differentiated Approach to Healthcare Risk Management
BlogCompliance
By CORL Technologies | April 17, 2025
2 Minute Read
Read Introducing CORL’s Core 4 Compliance Checklist: A Smarter Path to Healthcare Vendor Compliance
Infographics
INFOGRAPHIC Supply Chain Rocks! New Bills and Regulations Emerge Recent and forthcoming regulations and government guidance regarding cybersecurity and supply chains globally have spurred a sense of urgency for organizations to invest in compliance. In this infographic you will learn about: Download ‘Supply Chain Rocks: New Bills and Regulations Emerge’ infographic now. Want to download […]