BlogCompliance
Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment Suite
5 Minute Read
Read Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment SuiteCompliance
By CORL Technologies | November 14, 2022
The Cybersecurity and Infrastructure Security Agency (CISA) has been hinting for weeks about a pending announcement on cybersecurity for the nation’s critical infrastructure including healthcare. That update has arrived in the form of a major publication titled CPG: Cross-Sector Cybersecurity Performance Goals.[1]
The CPGs provide a mechanism for healthcare organizations and other critical sector entities to prioritize their implementation of the most effective and essential security controls required to defend against emerging cyberattacks.
This blog provides an overview of the CPGs and delves into the CPGs that are dedicated to supply chain and third-party vendor risk management. We also discuss the history and genesis of the CPGs, definitions and components, and practical applications for the CPGs for healthcare organizations.
Note: an audio summary overview of the CPGs is also available in our recent CyberPHIx podcast episode: CyberPHIx Roundup – Industry News and Trends for November, 2022.
President Biden issued several executive orders and national security memos in 2021 including Improving the Nation’s Cybersecurity and Improving Cybersecurity for Critical Infrastructure Control Systems.
The national security memo was issued following the high-profile cyberattack against the Colonial Pipeline that resulted in the declaration of a national security emergency. The memo required the CISA, in coordination with the National Institute of Standards and Technology (NIST) and the interagency community, to develop baseline cybersecurity performance goals, or CPGs, that are consistent across all critical infrastructure sectors.
The following resources published by CORL Technologies and our sister company, Meditology Services, provide more information about these presidential executive orders.
According to the CISA[2], the CPGs are “a prioritized subset of IT and operational technology (OT) cybersecurity practices that critical infrastructure owners and operators can implement to meaningfully reduce the likelihood and impact of known risks and adversary techniques. The goals were informed by existing cybersecurity frameworks and guidance, as well as the real-world threats and adversary tactics, techniques, and procedures (TTPs) observed by CISA and its government and industry partners. By implementing these goals, owners and operators will not only reduce risks to critical infrastructure operations, but also to the American people.”
The CPGs are intended to be:
The CISA comments up front that the CPGs are voluntary in nature. President Biden’s memo did not compel organizations to adopt the CPGs or provide reporting on them to any government agency. It would not be surprising if the CPGs were leveraged as part of future cybersecurity laws, but for now, they are voluntary.
The CISA acknowledges that the CPGs are not comprehensive in nature and are not designed to replace security control frameworks like NIST Cybersecurity Framework (NIST CSF). Rather, the CPGs are intended to provide a starting point for organizations to implement the most critical security controls first and to help prioritize remediation for areas that will have the greatest impact on thwarting the latest attack methods. The CPGs are mapped and aligned to the NIST CSF and are framed by the CISA as “a kind of QuickStart guide” for the NIST CSF.
The CPGs are organized into 8 categories or domains:
The CISA explained its selection criteria for how it chose the CPGs as follows:
Each CPG follows the same basic model that includes 6 data elements:
The CPG publication provides handy and practical materials to try to solve the “where do I begin problem” that so many healthcare organizations face when looking to adopt security frameworks. There is a downloadable Excel version of the CPGs that lists all CPGs and maps them back to other frameworks.
The publication also contains a worksheet with some components that would come in handy for a low-maturity organization. This worksheet contains tables that include all the data elements outlined above, but it also includes:
The CPG’s include a domain area dedicated to third-party vendor risk management (TPRM) for critical infrastructure industries including healthcare.
There are three CPGs, or requirements, under the Supply Chain / Third Party category:
The first supply chain CPG is focused on requiring healthcare organizations to conduct vendor risk assessments for cybersecurity capabilities and to institute preferential purchasing for vendors with stronger security controls.
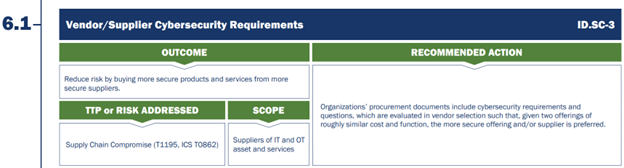
Figure 1 – CPG 6.1 Vendor / Supplier Cybersecurity Requirements
The second supply chain CPG is focused on requiring vendors to sign contractual agreements that commit to reporting cybersecurity incidents within a pre-defined “risk-informed” timeframe. This timeframe should be determined by the healthcare entity and documented via formal Service Level Agreements (SLAs) within vendor contracts.
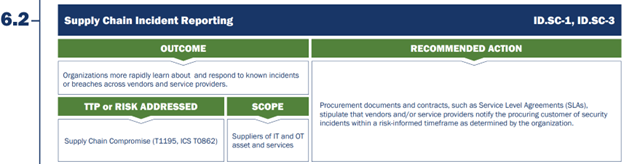
Figure 2 – CPG 6.2 Supply Chain Incident Reporting
The third, and final, supply chain CPG requires vendors to report confirmed security vulnerabilities to customers within a risk-informed timeframe. This requirement is similar to CPG 6.2 around incident reporting, but instead requires SLAs in contracts around vulnerability reporting.
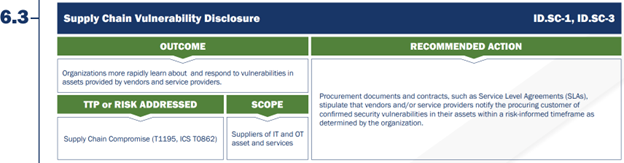
Figure 3 – CPG 6.3 Supply Chain Vulnerability Disclosure
CORL recommends that healthcare organizations of all shapes and sizes review the CPGs and leverage them to support and mature their cybersecurity and TPRM programs. CORL has also aligned our TPRM technology and managed services to reflect these CPG requirements around vendor security assessments, incident reporting, and vulnerability disclosure.
The CPGs are also about much more than third-party vendor risk management. For smaller organizations, the CPGs provide an excellent “on-ramp” to the adoption of larger, more complex security control frameworks like the NIST CSF or HITRUST. The CPGs provide the greatest “bang for the buck” in terms of cost-effective security controls that can greatly limit the likelihood and impact of cyberattacks.
For larger organizations, the CPGs are an excellent resource to prioritize ongoing assessment and remediation activities. The areas outlined in the CPGs should be prioritized above other assessment results to shore up security controls related to the latest threats and attack vectors facing the industry.
The CPG publication is one example of a series of high-quality publications that the CISA and other federal agencies have produced in recent months.
Contact our team here at CORL to learn more about the CPGs and how your organization can adopt and implement these controls to enhance your third-party vendor risk management program.
[1] https://www.cisa.gov/sites/default/files/publications/2022_00092_CISA_CPG_Report_508c.pdf
[2] https://www.cisa.gov/sites/default/files/publications/2022_00092_CISA_CPG_Report_508c.pdf
 CORL Technologies
CORL Technologies
CORL transforms TPRM chaos into clarity
CORL is a leading provider of vendor risk management solutions for the healthcare industry. CORL gets results by scaling organizational and vendor risk programs through our healthcare vendor risk clearinghouse solution, dashboard reporting that business owners can understand, and proven workflows that drive measurable risk reduction. CORL accelerates the speed of vendor risk assessments and holds vendors accountable for remediating risk exposures.
Related Posts
BlogCompliance
By CORL Technologies | June 24, 2025
5 Minute Read
Read Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment Suite
BlogCompliance
By CORL Technologies | April 23, 2025
2 Minute Read
Read The Power of Human + AI: CORL’s Differentiated Approach to Healthcare Risk Management
BlogCompliance
By CORL Technologies | April 17, 2025
2 Minute Read
Read Introducing CORL’s Core 4 Compliance Checklist: A Smarter Path to Healthcare Vendor Compliance
Webinars
WEBINAR AI + Healthcare: The Evolving Cybersecurity Equation The healthcare industry is undergoing a profound transformation, driven by the integration of artificial intelligence (AI) into various facets of healthcare delivery, diagnosis, and treatment. AI technology has the potential to revolutionize healthcare, improving care quality, reducing costs, enhancing efficiency, and even improving outcomes. However, with these […]