BlogCompliance
Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment Suite
5 Minute Read
Read Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment SuiteCybersecurity
By CORL Technologies | August 9, 2024
Vendors across sectors are crushed under the unforgiving weight of security questionnaires, but the burden is even heavier in healthcare cybersecurity, a sector in which the regulatory scrutiny is intense, and the cost of compromise is unrivaled. Security assessment questionnaires most often arise in the RFP process, but they can also emerge unexpectedly in the middle of a contract cycle as part of a customer’s internal third-party risk initiatives.
Long, unwieldy, and bespoke from one client to the next, responding to security questionnaires delays vendors from realizing revenue and monopolizes precious IT resources, detracting focus from other strategic IT initiatives. Vendors know the problem needs solving—but fluffy buzzwords and fragmentation in the solution landscape make it challenging to discern the right way forward. If you’re interested in key features for a cyber security assessment tool, make sure to read our last blog post.
In this blog post, we’ll discuss the available options for security questionnaire automation and unpack the advantages and shortcomings of each approach. This post will serve as a helpful evaluation guide for vendors who have long recognized the need to solve the security questionnaire dilemma but aren’t sure how.
Unpacking the real cost of security assessment questionnaires
Security assessment questionnaires slow the sales cycle—it’s true. While there is certainly a direct revenue cost associated with contract delays, there is also an indirect cost of security questionnaires that is perhaps even more substantial. Many healthcare vendors are operating with limited IT resources and budgets, forcing them to decide between answering security questionnaires and pursuing more strategic IT initiatives. Often, these IT initiatives are tied to risk reduction, which means that security questionnaires can quite literally inhibit a vendor’s ability to reduce risk. That is their ultimate irony.
Examining the options for vendors
The proliferation of technologies in healthcare contracting that are focused on risk management is both good and bad news for vendors. On one hand, the availability of security assessment tools empowers vendors to pursue an approach that is optimal for their organization, operational realities, and goals. On the other hand, clutter in the marketplace can add confusion to the decision-making process, as vendors navigate diverse alternatives that each claim to solve the problem in their own way.
If you are a salesperson or IT professional who is tired of responding to security questionnaires and determined to solve the problem once and for all, read on. What follows is a clear and candid description of the options available, and their specific advantages and drawbacks.
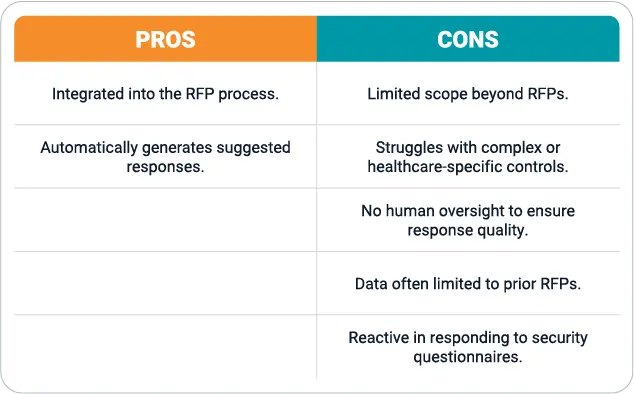
Option 1: Built-in questionnaire response in RFP tools
Many vendors believe built-in security assessment tools within their existing RFP platforms present an attractive solution. These tools are designed to seamlessly integrate with the RFP process. Security questionnaire automation allows vendors to quickly populate security questions within the context of a larger RFP response.
While these tools offer advantages in terms of seamlessness and efficiency, they also come with notable limitations that impact their effectiveness, particularly in the healthcare sector. For example, these tools are primarily designed for RFP scenarios and may not be as effective for questionnaires arising outside this context. This limitation can lead to inefficiencies when dealing with questionnaires that arise mid-contract or are ad-hoc in nature.
They also often lack the specialized healthcare cybersecurity knowledge and strategic view of risk required to effectively respond to complex healthcare-specific controls. More still, these solutions also lack a human element, which is crucial for more nuanced and context-specific responses. Despite the tremendous power of automation, generated responses can sometimes miss the mark, requiring hands-on refinement to prevent further inquiries and delays.
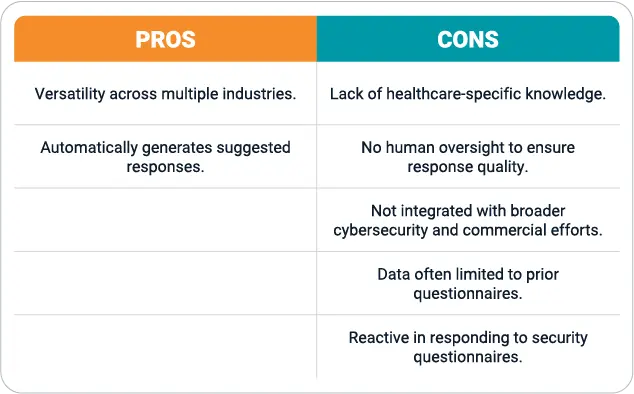
Option 2: Sector-agnostic security questionnaire response tools
Another option for vendors is to utilize a generic security questionnaire response tool that caters to a broad range of industries. Tools like these are designed to streamline response generation and offer versatility across various sectors, providing flexibility and utility. This makes them especially attractive to vendors operating in multiple industries. By leveraging advanced algorithms, these tools can quickly generate accurate answers to common questions, reducing the manual effort and time required to complete questionnaires.
However, while non-specific security assessment tools provide efficiency and broad applicability, they often fall short when it comes to addressing the specific regulatory and security needs of the healthcare industry. Generic responses may not satisfy healthcare clients’ stringent needs, which can erode trust and threaten deals. As with the first option, a persistent absence of human oversight can result in responses that lack depth and specificity.
While vendors may find some utility in sector-agnostic tools, those who sell heavily into healthcare will be left wanting due to the tool’s poor awareness of healthcare-specific regulations and requirements, and its lack of integration with the vendor’s other cybersecurity and commercial efforts.
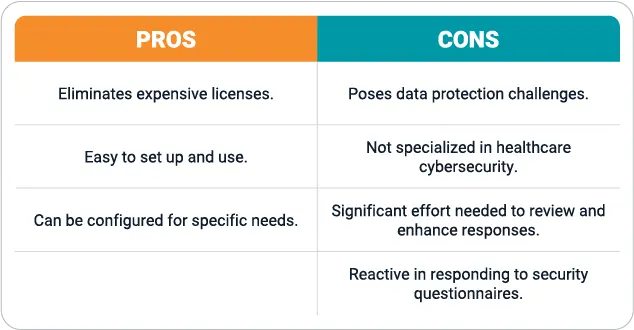
Option 3: Open-source AI security assessment tools
Open-source security assessment tools offer a budget-friendly option for vendors looking to automate responses. Without the need for costly licenses, vendors can allocate resources to other critical areas. Quick implementation and flexibility add to the appeal of these tools.
But harnessing an open-source tool comes with inherent risks and imitations, particularly in the highly sensitive healthcare cybersecurity domain. For instance, the use of open-source tools can raise security concerns regarding data usage and protection. Without the implementation of additional robust security measures, sensitive information could be at risk.
In addition, open-source tools are often based on AI models that are not specialized in cybersecurity at all. With the quality and rigor of a vendor’s security questionnaire responses serving as a gating factor in its ability to close a contract, this generalized approach is not sufficient. The vendor’s IT teams will often find themselves doing significant rework, or worse, spending outsized time and effort providing clarification to customers. These tools also lack human oversight, which is critically important even with the highest quality AI-generated responses.
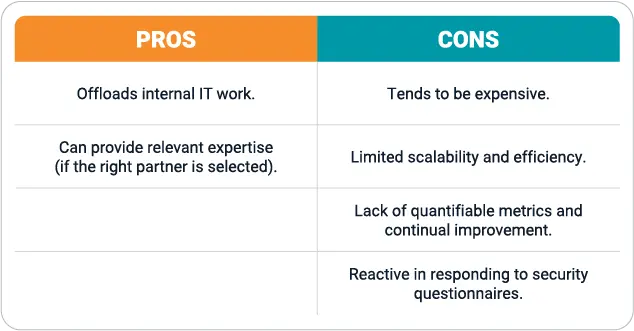
Option 4: Simple outsourcing
Some firms have rejected AI altogether, relying on simple outsourcing to take on the monotonous task of answering security questionnaires. But outsourcing can be expensive, and it is exceedingly challenging to find an outsourced firm that delivers the specialized healthcare cybersecurity knowledge and healthcare experience needed to deliver high-quality responses at scale.
This approach fails to apply human intervention only where it is most needed and neglects the radical time and cost savings that come with a secure and measured use of artificial intelligence. In addition, automation can be far more effective than humans at interpreting massive amounts of information quickly. By instantly interpreting existing documentation, a proper security questionnaire automation solution will rapidly surface insights that might be missed by a single outsourced contractor.
Finally, outsourcing fails to provide vendors quantifiable insights into the success of their collective security questionnaire response efforts—a key element in maximizing the efficiency and effectiveness of responses over time.
While each of these options has its own strengths and weaknesses, all of them are reactive—they respond to customer questions only after a formal questionnaire has been issued. An ideal solution will expedite questionnaire response while also reducing questionnaire volume by affirming a vendor’s suitability for contracting.
The solution: Healthcare security questionnaire automation with a human edge
For vendors overwhelmed by the complexities of security questionnaires in the healthcare contracting process, CORL provides a seamless and scalable solution that combines AI-driven automation with expert managed services. Here’s how.
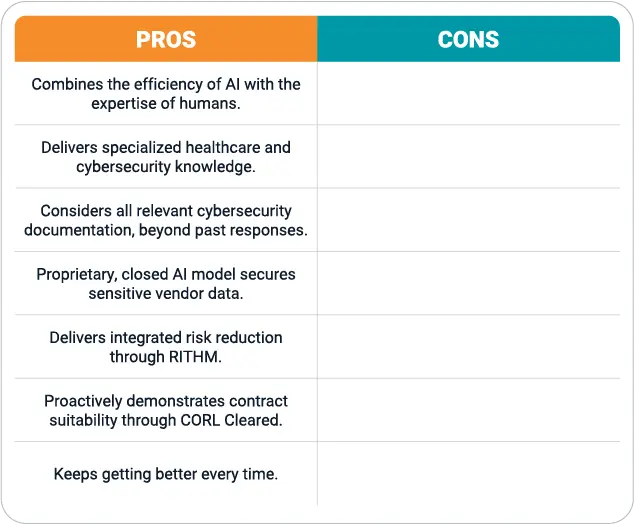
CORL Companion is a dynamic, healthcare-specialized solution for security questionnaire automation. A contrast to solutions that merely reuse or reinterpret prior questionnaires, CORL Companion harnesses all of a vendor’s relevant security documentation, including certifications, reports, profile data, and prior assessments, to generate contextually relevant responses in minutes. Specialized in both healthcare and cybersecurity, CORL Companion’s proprietary AI algorithm delivers relevant expertise and protects sensitive vendor data. Responses can be efficiently reviewed, refined, and submitted within the platform.
CORL combines Companion with hands-on, human-led support for security questionnaire automation, management, and remediation. RITHM, powered by Meditology, meets vendors where they are with an affordable subscription-based package of core healthcare cybersecurity, risk, and compliance services. In addition to tangibly reducing risk for vendors, RITHM generates documentation that can be harnessed to further enhance response quality.
But CORL does more than enhance the efficiency and quality of security questionnaire responses. Through CORL Cleared, CORL empowers vendors to proactively demonstrate their strong risk posture to prospects and customers alike. The CORL Cleared methodology consolidates disparate controls into a set of core risk indicators that are aligned with widely accepted assurances. The CORL Cleared designation is a powerful demonstration to healthcare organizations that a vendor’s cybersecurity practices are aligned with their requirements.
CORL’s solution addresses the security questionnaire response challenge from all angles—tactically through AI-enabled automation, strategically through expert-led support, and proactively through the CORL Cleared designation.
If you are interested in seeing CORL Companion live and learning how CORL accelerates the sales cycle for healthcare vendors, request a demo.
 CORL Technologies
CORL Technologies
CORL transforms TPRM chaos into clarity
CORL is a leading provider of vendor risk management solutions for the healthcare industry. CORL gets results by scaling organizational and vendor risk programs through our healthcare vendor risk clearinghouse solution, dashboard reporting that business owners can understand, and proven workflows that drive measurable risk reduction. CORL accelerates the speed of vendor risk assessments and holds vendors accountable for remediating risk exposures.
Related Posts
BlogCompliance
By CORL Technologies | June 24, 2025
5 Minute Read
Read Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment Suite
BlogCompliance
By CORL Technologies | April 23, 2025
2 Minute Read
Read The Power of Human + AI: CORL’s Differentiated Approach to Healthcare Risk Management
BlogCompliance
By CORL Technologies | April 17, 2025
2 Minute Read
Read Introducing CORL’s Core 4 Compliance Checklist: A Smarter Path to Healthcare Vendor Compliance
Webinars
WEBINAR AI + Healthcare: The Evolving Cybersecurity Equation The healthcare industry is undergoing a profound transformation, driven by the integration of artificial intelligence (AI) into various facets of healthcare delivery, diagnosis, and treatment. AI technology has the potential to revolutionize healthcare, improving care quality, reducing costs, enhancing efficiency, and even improving outcomes. However, with these […]