BlogCompliance
Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment Suite
5 Minute Read
Read Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment SuiteCybersecurity
By CORL Technologies | April 21, 2022
Cyber criminals and nation states have unleashed relentless cyber-attacks on the U.S. healthcare industry and its suppliers this year. Healthcare organizations have their hands full trying to build and sustain third-party vendor risk management programs to grapple with the burgeoning scope and scale of cybersecurity risk exposures presented by their vendors.
Unfortunately, cyber risk exposures have not been limited to third-party vendors and risks to sensitive data and systems often extend across the full supply chain including fourth-party vendors and open-sourced products.
This blog post provides insights into the growing risks associated with fourth-party vendors and applications that many healthcare organizations have not yet addressed. The objective of this publication is to level set definitions for fourth-party risk, outline current risk mitigation models and challenges, and propose innovative approaches for mitigating supply chain risks that extend to fourth parties.
Every healthcare organization outsources parts of its operations to multiple suppliers, which are commonly referred to as third parties. Those third-party suppliers, in turn, outsource their operations
to other suppliers, which are commonly referred to as fourth parties.
Fourth parties can include companies or open-sourced products and platforms.
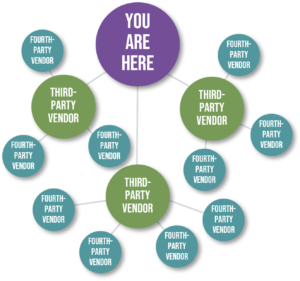
Some examples of common fourth-party vendors and platforms include:
Cyber-criminal gangs and nation states like Russia have realized that they can take advantage of the widespread adoption of fourth-party vendors and applications to scale their attacks across entire industry segments. One compromised fourth-party vendor can lead to the compromise of thousands of organizations.
Cyber-criminal syndicates operate as a business and are always looking for ways to maximize their return on investment for the people and tools required to convert cyber breaches into cash. Once an organization has been compromised via a fourth-party application, malicious actors are then free to launch a variety of attacks including ransomware, data theft, extortion, and more.
This approach of targeting fourth-party products and services can be characterized as a “hack once, breach many” strategy. As a result, breaches to fourth-party suppliers have a cascading risk impact to the industry.
Prominent examples of recent fourth-party breaches impacting healthcare organizations include:
Healthcare organizations are struggling to manage third-party risks; fourth-party risks are barely on the radar. The industry is still scrambling to build processes and technology to help inventory, assess, and manage risks for third-party vendors. Proactive fourth-party risk management is getting little to no investment due to the focus on third-parties and the lack of bandwidth to tackle fourth-party vulnerabilities.
At the heart of the problem is the fact that that healthcare entities have little to no visibility into fourth-party relationships. When a large-scale fourth-party vendor breach occurs like the Log4j or SolarWinds, healthcare organizations are unable to assess which third-party vendors may be impacted and are therefore unable to take appropriate action.
Very few third-party vendors maintain accurate inventories of their own supply chain vendors and products. As a result, supply chain vendors often get overwhelmed with assessments and inquiries during large-scale fourth-party breach events.
The sheer volume of third- and fourth-party suppliers and products has also overwhelmed third-party risk management teams for healthcare entities.
The impacts of fourth-party supply chain attacks have not been limited to healthcare organizations. The U.S. federal government has been taking steps to help defend critical infrastructure, federal, and private sector organizations from supply chain risks.
President Biden issued sweeping executive orders on supply chain risk in response to SolarWinds attack that have been helping to establishing standards for inventorying third- and fourth-party vendors including the adoption of Software Bill of Materials (SBOM) models.
A software Bill of Materials (SBOM) is a list or inventory of all third- and fourth-party components used to deliver a product or solution. An SBOM can be thought of like an ingredients list for software or hardware.
The advantage of an SBOM is that it allows organizations to quickly assess and respond to supply chain breaches by identifying which products and services use the breached software or product.
An oversimplified example of an SBOM for a medical device product would be a listing of sub-components such as:
SBOMs alone will not solve fourth-party risks, but they are an important first step in gaining visibility into the impacted systems and vendors that require attention.
Our organization, CORL Technologies, has been continually innovating new technology and processes designed to drive industry-wide responses to fourth-party risks that create speed in visibility and risk mitigation activities.
When a fourth-party breach is reported, CORL:
A recent example of CORL’s response to industry-wide supply chain breach events is the cyberwar stemming from Russia’s invasion of Ukraine. In this case, CORL leveraged our data to identify vendors
with presence or assets in the region. We worked with customers to identify which of their third- and fourth-party vendors and products may have been exposed.
CORL also worked with our customers to prioritize vendors based on criticality and defined remediation & mitigation plans for those vendors and products.
CORL continues to incorporate and develop additional fourth-party risk management capabilities into our software solution. Stay tuned to CORL’s resource center as we deploy new functionality this year to help healthcare organizations mitigate risks associated with fourth-party vendors and products.
Contact our team here at CORL to learn more about our managed services and next generation exchange for healthcare vendor risk data that gets results and lowers third- and fourth-party risks.
 CORL Technologies
CORL Technologies
CORL transforms TPRM chaos into clarity
CORL is a leading provider of vendor risk management solutions for the healthcare industry. CORL gets results by scaling organizational and vendor risk programs through our healthcare vendor risk clearinghouse solution, dashboard reporting that business owners can understand, and proven workflows that drive measurable risk reduction. CORL accelerates the speed of vendor risk assessments and holds vendors accountable for remediating risk exposures.
Related Posts
BlogCompliance
By CORL Technologies | June 24, 2025
5 Minute Read
Read Unlocking Vendor Assurance: A Deep Dive into CORL Technologies’ Assessment Suite
BlogCompliance
By CORL Technologies | April 23, 2025
2 Minute Read
Read The Power of Human + AI: CORL’s Differentiated Approach to Healthcare Risk Management
BlogCompliance
By CORL Technologies | April 17, 2025
2 Minute Read
Read Introducing CORL’s Core 4 Compliance Checklist: A Smarter Path to Healthcare Vendor Compliance
Webinars
WEBINAR AI + Healthcare: The Evolving Cybersecurity Equation The healthcare industry is undergoing a profound transformation, driven by the integration of artificial intelligence (AI) into various facets of healthcare delivery, diagnosis, and treatment. AI technology has the potential to revolutionize healthcare, improving care quality, reducing costs, enhancing efficiency, and even improving outcomes. However, with these […]